By now, most people have understood that they shouldn’t just click on every link anymore. Malware of any kind could hide behind it. But most social media platforms and chat providers offer a very elegant way to present trustworthy looking links: the link preview cards. These represent a preview of the link target by already displaying the image and parts of the text. This makes them appear far more trustworthy than regular links without this preview. This makes people click on them more easily. But there’s a problem: these preview cards can easily be faked. Such an attack is known as social media link preview spoofing.
Here is an example of such a preview card from the BBC news page inside of a Telegram channel:
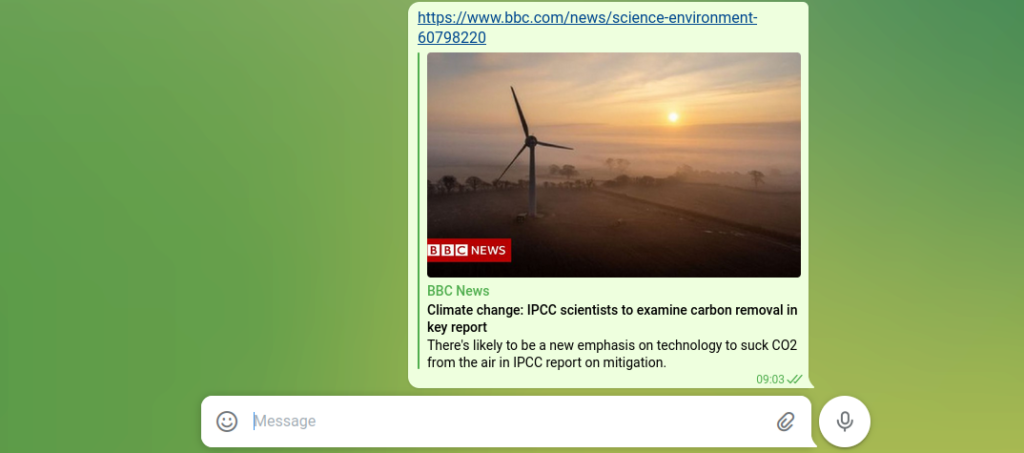
How are these cards generated?
In order to understand how such preview cards are generated, it is important to understand how they are generated by the platforms or chat services.
Ultimately, it’s quite simple: As soon as a URL is published in a post or chat, the provider calls it up independently and reads some metadata from the target website. These data are usually stored in a cache. So if the link is posted somewhere again, the card will not be regenerated but taken from this cache.
The following meta information in the source code of the target page is used to generate such links. Different services sometimes use different meta information. As a result, double data sometimes occurs here:
<meta property="og:description" content="There's likely to be a new emphasis on technology to suck CO2 from the air in IPCC report on mitigation."/>
<meta property="og:image" content="https://ichef.bbci.co.uk/news/1024/branded_news/A6D2/production/_123760724_gettyimages-1365916256.jpg"/>
<meta property="og:image:alt" content="IPCC"/>
<meta property="og:locale" content="en_GB"/>
<meta property="og:site_name" content="BBC News"/>
<meta property="og:title" content="Climate change: IPCC scientists to examine carbon removal in key report"/>
<meta property="og:type" content="article"/>
<meta property="og:url" content="https://www.bbc.com/news/science-environment-60798220"/>
<meta name="twitter:card" content="summary_large_image"/>
<meta name="twitter:creator" content="@BBCWorld"/>
<meta name="twitter:description" content="There's likely to be a new emphasis on technology to suck CO2 from the air in IPCC report on mitigation."/>
<meta name="twitter:domain" content="www.bbc.com"/>
<meta name="twitter:image:src" content="https://ichef.bbci.co.uk/news/1024/branded_news/A6D2/production/_123760724_gettyimages-1365916256.jpg"/>
<meta name="twitter:image:alt" content="IPCC"/>
<meta name="twitter:site" content="@BBCWorld"/>
<meta name="twitter:title" content="Climate change: IPCC scientists to examine carbon removal in key report"/>
How can such a preview be faked?
The social media or chat provider cannot know if this meta information is real. So there is no verification. For example, you could easily integrate the metadata shown above into your own website. If you then share a link, the same preview card would be generated. But it would link to your own (maybe malicious) website.
Warmup the cache
On most platforms, the preview doesn’t appear immediately after you post a link. Because in the background, the servers first have to visit the target website and generate the preview. If you do not want your link to be displayed without a preview during this time (because it looks suspicious, for example), you must first post it inside a hidden channel of the platform. This can be, for example, a private group with only one person or a private account. This way, the next time you post the link, the card will immediately appear in your target channel because it was already generated.
Hide the target link
There is one thing that cannot be faked: The destination link. Some platforms show the target link directly. In these cases, however, URL shorteners such as shorturl.at can help. There you can store your target URL and thus disguise the original link. This does not affect the generation of preview cards, as these are always generated from the last destination in a forwarding chain.
Make the landing page look realistic
You definitely want to avoid having your links or account reported or banned by the providers. Therefore, it is very important that the target links look unobtrusive and, if possible, show the original content. This is mostly very simple and there are different options for it:
- Many sites don’t set an X-Frame-Options header. This means your own website can easily embed these pages as fullscreen I-frames.
- If your malware works fast enough, you can quickly redirect to the original site from your site.
- You can use a server-side proxy to retrieve the original contents from a website and display it on your own page.
Conclusion
As you can see, you shouldn’t trust preview cards either. They can be easily faked and even the landing pages can be made realistic with little effort. For this reason you should always be very skeptical. Especially when URL shorteners are used.
Title image: https://pixabay.com/de/photos/internet-whatsapp-smartphone-3113279/
